Did you know that innocent-looking links can secretly hijack your browser tabs? Learn how reverse tabnapping works, why it’s dangerous, and how to protect yourself and your users.
Introduction
At XoHub Solutions, we prioritize web security—and one often-overlooked threat is reverse tabnapping (or tabnabbing). This phishing attack exploits a simple HTML attribute to trick users into entering sensitive data on fake pages.
In this guide, we’ll cover:
✔ What reverse tabnapping is
✔ How hackers exploit it
✔ Real-world risks
✔ How to prevent it (for developers & users)
Let’s dive in!
What is Reverse Tabnapping?
Reverse tabnapping is a phishing technique where a malicious website silently changes the original tab to a fake login page after a user clicks a link.
How It Works:
1️⃣ A user clicks a link with target="_blank" (opens in a new tab).
2️⃣ The malicious page accesses window.opener (JavaScript).
3️⃣ It rewrites the original tab to a phishing page (e.g., fake Gmail login).
4️⃣ When the user switches back, they unknowingly enter credentials into a fake site.
Example Attack Scenario:
- You open a link from a trusted blog in a new tab.
- You browse the new tab, then return to the original page.
- Instead of the blog, you see a fake Google login—but the URL looks correct!
Technical Explanation
The Vulnerable Code
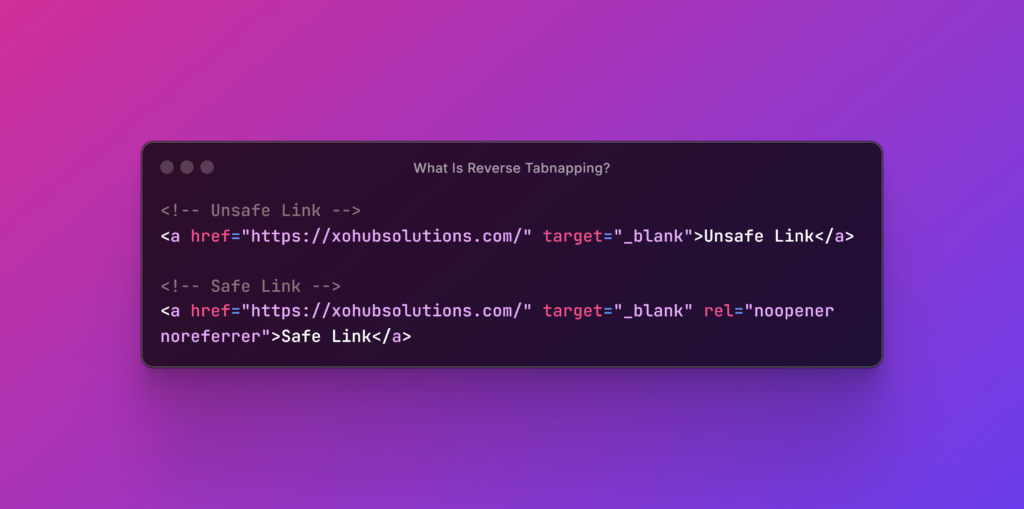
<!-- UNSAFE: Allows reverse tabnapping --> <a href="https://malicious-site.com" target="_blank">Click Me</a>
Problem: Without rel="noopener noreferrer", the new tab can control the original page via window.opener.
The Malicious Script
if (window.opener) {
window.opener.location = "https://fake-login.com";
}
This replaces the original tab’s URL with a phishing page.
🚨 Why Is This Dangerous?
- No warnings – Happens silently in the background.
- Affects trusted sites – Even legitimate sites can be compromised.
- Steals credentials – Fake login pages capture passwords, credit cards, etc.
- Hard to detect – Users don’t realize they’ve been tricked.
How to Prevent Reverse Tabnapping?
For Developers:
Always use rel="noopener noreferrer"
<a href="https://example.com" target="_blank" rel="noopener noreferrer">Safe Link</a>
noopener→ Blockswindow.openeraccess.noreferrer→ Hides referral data (extra security).
Modern Browsers Help
Chrome, Firefox, and Edge now automatically set noopener, but explicitly adding it is best practice.
For Website Owners & Users:
✔ Use security extensions (uBlock Origin, NoScript).
✔ Check URLs before clicking (hover over links).
✔ Keep browsers updated (latest security patches).
Real-World Impact
| Case | What Happened? |
|---|---|
| Fake Bank Login | Attackers replaced a banking site with a phishing page. |
| Social Media Scam | Users thought they were logging into Facebook—but it was fake. |
| E-Commerce Fraud | Hackers stole credit card details via fake checkout pages. |
Conclusion
Reverse tabnapping is a silent but dangerous threat—but the fix is simple!


Thanks a lot very helpful